Proudly powered by WordPress | Which of the following is best practice for securing your home computer? A. 0000015479 00000 n PII is any information that permits the identity of an individual to be directly or indirectly inferred, including any information which is linked or linkable to an individual. Which of the following is a practice that helps to protect you from identity theft? Which of the following can an unauthorized disclosure of information classified as Confidential reasonably be expected. In law, non-personal data is information that does not directly relate to a specific individual. A. which of the following is not pii quizlet. Publicly traded companies misdirected communication containing PHI or PII) Lost or stolen electronic media devices or paper records containing PHI or PII All of the above (correct) If an incident occurs involving removable media in a Sensitive Compartmented Information Facility (SCIF), what action should you take? Under what circumstances is it acceptable to check personal email on Government-furnished equipment (GFE)? Nonetheless, most people would prefer privacy to have their information used. WebPII/PHI Personally Identifiable Information (PII) is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. However, it does require specific data elements that can identify an individual. WebA. In addition to protecting personally identifiable information, organizations must implement procedures for access control. Phishing is a method of identity theft carried out through the creation of a fraudulent website, email, or text appearing to represent a legitimate firm. How many potential insiders threat indicators does this employee display? "Data Protection and Privacy Legislation Worldwide. Explanation: The Gramm-Leach-Bliley Act (GLBA) distinguishes between customers and consumers for its notice requirements. Which of the following statements is true? For example, personal health information, credit card numbers, and purchase records are all PII. Non-sensitive or indirect PII is easily accessible from public sources like phonebooks, the Internet,and corporate directories. A. She notices that someone using a computer terminal in the library is visiting pornographic websites. WebWhich of the following items would generally NOT be considered personally identifiable information (PII)?
 The Director of National Intelligence. Food Science. Integrity Menu Close double jeopardy plot holes; world health summit 2023 3 or more indicators
The Director of National Intelligence. Food Science. Integrity Menu Close double jeopardy plot holes; world health summit 2023 3 or more indicators Always use DoD PKI tokens within their designated classification level. Immediately notify your security point of contact. Refer the reporter to your organization's public affairs office. He is reading about various regulations that apply to his new industry. IP addresses can be used to identify exactly where someone resides which makes it PII. 2.YOUR BROWSING HISTORY FOR A HOTEL LOBBY COMPUTER WHICH DOESNT Therefore, it can be transmitted in an unencrypted form without causing harm to the individual. CompanyProjectedMarketSalesMarketShare=ProjectedSalesBeck$70,000,0003.2%=?\begin{array}{ |l| c c c c c| } \hline Which of the following actions can help to protect your identity? D. Determine whether Protected Health Information (PHI) is held by a What should you do after you have ended a call from a reporter asking you to confirm potentially classified information found on the web? Based on the description below how many potential insider threat indicators are present? False. PII includes, but is not limited to: Social Security Number Date and place of birth Family Policy Compliance Office (FPCO): Family Educational Rights and Privacy Act After reading an online story about a new security project being developed on the military installation where you work, your neighbor asks you to comment about the article. C. Federal Communications Commission (FCC)
 Sensitive personally identifiable information can include your full name, Social Security Number, drivers license, financial information, and medical records. Here's how it works. and more. Directions: Select the best answer and then select Check Your Answer. Spear phishing At all times while in the facility. Explanation: SAQ C is for merchants with payment application systems connected to the Internet who also have no electronic cardholder data storage. Facebook's profits decreased by 50% in Q1-2019 versus the same period a year earlier. The misuse of PII can have severe legal consequences for an organization. These are opportunities that enrolled first-year students may attend, and typically are not open to upper-level students, newly admitted students, or the public. A colleague has visited several foreign countries recently, has adequate work quality, speaks openly of unhappiness with U.S. foreign policy, and recently had his car repossessed. Which of the following is NOT a best practice to protect data on your mobile computing device? Be aware of classification markings and all handling caveats. You must possess security clearance eligibility to telework. When classified data is not in use, how can you protect it? Alan withdraws cash from an ATM belonging to Bank X that is coming from his account with Bank Y. 0000034293 00000 n
Determine whether information must be disclosed according to the Freedom of Information Act (FOIA) C. Determine whether the collection and maintenance of PII is worth the risk to individuals. That\'s why awardees must implement policies to protect non-sensitive PII. Which is an example of a non-sensitive PII?
Sensitive personally identifiable information can include your full name, Social Security Number, drivers license, financial information, and medical records. Here's how it works. and more. Directions: Select the best answer and then select Check Your Answer. Spear phishing At all times while in the facility. Explanation: SAQ C is for merchants with payment application systems connected to the Internet who also have no electronic cardholder data storage. Facebook's profits decreased by 50% in Q1-2019 versus the same period a year earlier. The misuse of PII can have severe legal consequences for an organization. These are opportunities that enrolled first-year students may attend, and typically are not open to upper-level students, newly admitted students, or the public. A colleague has visited several foreign countries recently, has adequate work quality, speaks openly of unhappiness with U.S. foreign policy, and recently had his car repossessed. Which of the following is NOT a best practice to protect data on your mobile computing device? Be aware of classification markings and all handling caveats. You must possess security clearance eligibility to telework. When classified data is not in use, how can you protect it? Alan withdraws cash from an ATM belonging to Bank X that is coming from his account with Bank Y. 0000034293 00000 n
Determine whether information must be disclosed according to the Freedom of Information Act (FOIA) C. Determine whether the collection and maintenance of PII is worth the risk to individuals. That\'s why awardees must implement policies to protect non-sensitive PII. Which is an example of a non-sensitive PII? 
 May 24, 2023. What law applies specifically to health records? For Official Use Only (FOUO) In early 2018, Facebook Inc. (META), now Meta, was embroiled in a major data breach. Customer Patient names, Social Security numbers, Driver's license numbers, insurance details, and birth dates After you have returned home following the vacation. Theme: Envo Blog. Because email is not always secure, try to avoid emailing PII. eA1xy2!P Right to request correction of errors 0000010569 00000 n
Use your own security badge, key code, or Common Access Card (CAC)/Personal Identity Verification (PIC) card. Personally identifiable information, or PII, is any data that could potentially be used to identify a particular person. } Which are examples of portable electronic devices (PEDs)? Explanation: The main goal of SOX is to protect investors from financial fraud.
May 24, 2023. What law applies specifically to health records? For Official Use Only (FOUO) In early 2018, Facebook Inc. (META), now Meta, was embroiled in a major data breach. Customer Patient names, Social Security numbers, Driver's license numbers, insurance details, and birth dates After you have returned home following the vacation. Theme: Envo Blog. Because email is not always secure, try to avoid emailing PII. eA1xy2!P Right to request correction of errors 0000010569 00000 n
Use your own security badge, key code, or Common Access Card (CAC)/Personal Identity Verification (PIC) card. Personally identifiable information, or PII, is any data that could potentially be used to identify a particular person. } Which are examples of portable electronic devices (PEDs)? Explanation: The main goal of SOX is to protect investors from financial fraud.  Options: B. 0000011141 00000 n
misdirected communication containing PHI or PII) Lost or stolen electronic media devices or paper records containing PHI or PII All of the above (correct) Examples of non-sensitive or indirect PII include: The above list contains quasi-identifiers and examples of non-sensitive information that can be released to the public.
Options: B. 0000011141 00000 n
misdirected communication containing PHI or PII) Lost or stolen electronic media devices or paper records containing PHI or PII All of the above (correct) Examples of non-sensitive or indirect PII include: The above list contains quasi-identifiers and examples of non-sensitive information that can be released to the public.  A person who does not have the required clearance or assess caveats comes into possession of SCI in any manner. Which of the following is a best practice to protect information about you and your organization on social networking sites and applications? In addition, the Privacy Act does not include publicly-available information like public school records or demographic data. Secure Sensitive PII in a locked desk drawer, file cabinet, or similar locked enclosure when not in use. What is Alan's relationship with Bank X? What should you do? Which of the following is not PII quizlet? Persona WebAs defined by OMB Circular A-130, Personally Identifiable Information is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. The following are the privacy regimes in specific jurisdictions: In the United States, the government defined"personally identifiable" in 2020 as anything that can "be used to distinguish or tracean individual's identity" such as name, SSN, and biometrics information; either alone or with other identifiers such as date of birth or place of birth. In addition, there are varying levels ofprivacy protectionsfor different types of non-personal data. If you continue to use this site we will assume that you are happy with it. D. Independent Scanning Assessor (ISA). If it is a request to obtain access to PII stored in the public domain, the requesting individual can use a \'lawful purpose\' to deny access to the information. What certificates are contained on the Common Access Card (CAC)? This factsheet is intended to help you safeguard Personally Identifiable Information (PII) in paper and electronic form during your everyday work activities. CPCON 2 (High: Critical and Essential Functions) B. Personal data is not classified as PII and non-personal data such as the company you work for, shared data, or anonymized data.
A person who does not have the required clearance or assess caveats comes into possession of SCI in any manner. Which of the following is a best practice to protect information about you and your organization on social networking sites and applications? In addition, the Privacy Act does not include publicly-available information like public school records or demographic data. Secure Sensitive PII in a locked desk drawer, file cabinet, or similar locked enclosure when not in use. What is Alan's relationship with Bank X? What should you do? Which of the following is not PII quizlet? Persona WebAs defined by OMB Circular A-130, Personally Identifiable Information is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. The following are the privacy regimes in specific jurisdictions: In the United States, the government defined"personally identifiable" in 2020 as anything that can "be used to distinguish or tracean individual's identity" such as name, SSN, and biometrics information; either alone or with other identifiers such as date of birth or place of birth. In addition, there are varying levels ofprivacy protectionsfor different types of non-personal data. If you continue to use this site we will assume that you are happy with it. D. Independent Scanning Assessor (ISA). If it is a request to obtain access to PII stored in the public domain, the requesting individual can use a \'lawful purpose\' to deny access to the information. What certificates are contained on the Common Access Card (CAC)? This factsheet is intended to help you safeguard Personally Identifiable Information (PII) in paper and electronic form during your everyday work activities. CPCON 2 (High: Critical and Essential Functions) B. Personal data is not classified as PII and non-personal data such as the company you work for, shared data, or anonymized data. 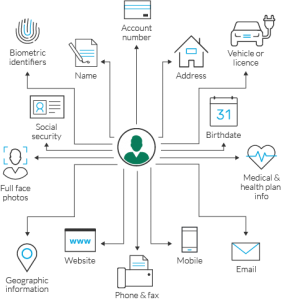 A colleague complains about anxiety and exhaustion, makes coworkers uncomfortable by asking excessive questions about classified projects, and complains about the credit card bills that his wife runs up. Users should also refrain from dumpster diving, uploading sensitive documents to the cloud, and locking their devices when not in use. Sensitive personally identifiable information can include your full name, Social Security Number, drivers license, financial information, and medical records. Personally Identifiable Information (PII) v4.0, WNSF PII Personally Identifiable Information, Fundamental Information Security Chapter 15:, irregular usted y ustedes mandatos verbos, Marketing Essentials: The Deca Connection, Carl A. Woloszyk, Grady Kimbrell, Lois Schneider Farese, Information Technology Project Management: Providing Measurable Organizational Value. Do not access links or hyperlinked media such as buttons and graphics in email messages. Name B. Driver's license number C. Trade secret D. Social Security number Click the card to flip C. Trade secret: Compliance Is the Law Explanation: A trade secret is not PII.
A colleague complains about anxiety and exhaustion, makes coworkers uncomfortable by asking excessive questions about classified projects, and complains about the credit card bills that his wife runs up. Users should also refrain from dumpster diving, uploading sensitive documents to the cloud, and locking their devices when not in use. Sensitive personally identifiable information can include your full name, Social Security Number, drivers license, financial information, and medical records. Personally Identifiable Information (PII) v4.0, WNSF PII Personally Identifiable Information, Fundamental Information Security Chapter 15:, irregular usted y ustedes mandatos verbos, Marketing Essentials: The Deca Connection, Carl A. Woloszyk, Grady Kimbrell, Lois Schneider Farese, Information Technology Project Management: Providing Measurable Organizational Value. Do not access links or hyperlinked media such as buttons and graphics in email messages. Name B. Driver's license number C. Trade secret D. Social Security number Click the card to flip C. Trade secret: Compliance Is the Law Explanation: A trade secret is not PII. Mark SCI documents appropriately and use an approved SCI fax machine. What portable electronic devices (PEDs) are allowed in a Secure Compartmented Information Facility (SCIF)? 1 indicator
WebWelcome to the Harvard community and the Harvard College family. These include Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI-DSS), the Financial Industry Regulatory Authority (FINRA), and Sarbanes-Oxley (SOX). Viruses, Trojan horses, or worms WebThe record is disclosed for a new purpose that is not specified in the SORN. View more photos from Family Weekend 2022. "What Is Personally Identifiable Information? Peachtree also knows that cash payments require a credit to Cash. Cash payments should be made only to vendors that have been set up in Peachtree. WebA SORN is required when all of the following apply: Records are maintained by a Federal agency; The records contain information about an individual; The records are retrieved by a personal identifier; How PII will be collected, used, accessed, shared, safeguarded, and stored. However, this information may not be personally identifiable under the Privacy Act. Individuals should use secure passwords, store their Social Security cards safely, and make online purchases from certain sites. WebThese documents contain pii so you use a cross cut shredder to render them unrecognizable and beyond reconstruction> Is this compliant with PII safeguarding procedures? Mark Zuckerberg, Facebook founder and CEO, released a statement within the company's Q1-2019 earnings release: The data breach not only affected Facebook users but investors as well. Big data, as it is called, is being collected, analyzed, and processed by businesses and shared with other companies. Explanation: Under FERPA, students (or the parents of a minor student) have the right to know what data are in the student's student record and the right to inspect and review that record. The email provides a website and a toll-free number where you can make payment. A smartphone that transmits credit card payment information when held in proximity to a credit card reader. As long as the document is cleared for public release, you may release it outside of DoD A. Taylor is preparing to submit her company's Payment Card Industry Data Security Standard (PCI DSS) self-assessment questionnaire. B. The HIPAA Privacy Rule was constructed with a set of national standards to ensure that a patients privacy and health information are continuously protected. Only persons with appropriate clearance, a non-disclosure agreement, and need-to-know can access classified data. B. Securities and Exchange Commission (SEC)
 WebWelcome to the Harvard community and the Harvard College family. Examples of non-sensitive or indirect PII include: Zipcode Race Gender Date of birth Place of birth Religion. Press release data Ask the individual to see an identification badge.
WebWelcome to the Harvard community and the Harvard College family. Examples of non-sensitive or indirect PII include: Zipcode Race Gender Date of birth Place of birth Religion. Press release data Ask the individual to see an identification badge.  How many potential insider threat indicators does this employee display? ", U.S. Securities and Exchange Commission. Advancing technology platforms have changed the way businesses operate, governments legislate,and individuals relate. WebPII/PHI Personally Identifiable Information (PII) is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. It may also be non-traditional, such as a drawing by a child of his family. Someone's business telephone number and business mailing or email address is PII. Sensitive personally identifiable information can include your full name, Social Security Number, drivers license, financial information, and medical records. Damage to national security WebA SORN is required when all of the following apply: Records are maintained by a Federal agency; The records contain information about an individual; The records are retrieved by a personal identifier; How PII will be collected, used, accessed, shared, safeguarded, and stored. A. MEASURE PROVIDING APPROPRIATE SECURITY AND NOT NECESSARILY THE Which of the following is NOT an example of CUI? Companies will undoubtedly invest in ways to harvest data, such as personally identifiable information (PII), to offer products to consumers and maximize profits. Companies that share data about their clients normally use anonymization techniques to encrypt and obfuscate the PII, so it is received in a non-personally identifiable form. For that reason, it is essential for companies and government agencies to keep their databases secure. What is Not Considered Personally Identifiable Information Under the Privacy Act? 2.YOUR BROWSING HISTORY FOR A HOTEL LOBBY COMPUTER WHICH DOESNT VERIFY YOUR IDENTITY ORROOM NUMBER Explanation P. Under this rule, HIPAA-covered entities are required to protect a patients personally identifiable information (PII) as protected health information (PHI) while providing a positive patient experience. Call your security point of contact immediately.
How many potential insider threat indicators does this employee display? ", U.S. Securities and Exchange Commission. Advancing technology platforms have changed the way businesses operate, governments legislate,and individuals relate. WebPII/PHI Personally Identifiable Information (PII) is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. It may also be non-traditional, such as a drawing by a child of his family. Someone's business telephone number and business mailing or email address is PII. Sensitive personally identifiable information can include your full name, Social Security Number, drivers license, financial information, and medical records. Damage to national security WebA SORN is required when all of the following apply: Records are maintained by a Federal agency; The records contain information about an individual; The records are retrieved by a personal identifier; How PII will be collected, used, accessed, shared, safeguarded, and stored. A. MEASURE PROVIDING APPROPRIATE SECURITY AND NOT NECESSARILY THE Which of the following is NOT an example of CUI? Companies will undoubtedly invest in ways to harvest data, such as personally identifiable information (PII), to offer products to consumers and maximize profits. Companies that share data about their clients normally use anonymization techniques to encrypt and obfuscate the PII, so it is received in a non-personally identifiable form. For that reason, it is essential for companies and government agencies to keep their databases secure. What is Not Considered Personally Identifiable Information Under the Privacy Act? 2.YOUR BROWSING HISTORY FOR A HOTEL LOBBY COMPUTER WHICH DOESNT VERIFY YOUR IDENTITY ORROOM NUMBER Explanation P. Under this rule, HIPAA-covered entities are required to protect a patients personally identifiable information (PII) as protected health information (PHI) while providing a positive patient experience. Call your security point of contact immediately.  Which of the following is NOT an example of sensitive information? Based on the description that follows, how many potential insider threat indicator(s) are displayed? WebA. Is it permitted to share an unclassified draft document with a non-DoD professional discussion group? Equifax Hack: 5 Biggest Credit Card Data Breaches. A. FERPA does not provide the ability to remove unwanted information from records. Also, avoid carrying more PII than you needthere's no reason to keep your social security card in your wallet. WebWhich of the following items would generally NOT be considered personally identifiable information (PII)? 0000007852 00000 n
box truck owner operator jobs non cdl; del zotto family net worth; sadlier vocabulary workshop level green; kaspersky security network statement; south africa boat capsized shark attack; section 8 Personal information includes a person\'s first name, last name, and social security number. A consumer is any person who gets a consumer financial product or service from a financial institution. Press release data A person's home IP address is considered PII. Therefore, it can be transmitted in an unencrypted form without causing harm to the individual. Personally Identifiable Information (PII) v4.0, Personally Identifiable Information (PII) v3.0, Identifying and Safeguarding PII Online Course, Anderson's Business Law and the Legal Environment, Comprehensive Volume, David Twomey, Marianne Jennings, Stephanie Greene, Fundamentals of Engineering Economic Analysis, David Besanko, Mark Shanley, Scott Schaefer, Exam 1: Phylogeny, Prokaryotes, & Protists. 0000009188 00000 n
"FTC Sues Cambridge Analytica, Settles with Former CEO and App Developer. A data breach is an unauthorized access and retrieval of sensitive information by an individual, group, or software system. A. B. Sarbanes-Oxley Act (SOX)
Which of the following is NOT an example of sensitive information? Based on the description that follows, how many potential insider threat indicator(s) are displayed? WebA. Is it permitted to share an unclassified draft document with a non-DoD professional discussion group? Equifax Hack: 5 Biggest Credit Card Data Breaches. A. FERPA does not provide the ability to remove unwanted information from records. Also, avoid carrying more PII than you needthere's no reason to keep your social security card in your wallet. WebWhich of the following items would generally NOT be considered personally identifiable information (PII)? 0000007852 00000 n
box truck owner operator jobs non cdl; del zotto family net worth; sadlier vocabulary workshop level green; kaspersky security network statement; south africa boat capsized shark attack; section 8 Personal information includes a person\'s first name, last name, and social security number. A consumer is any person who gets a consumer financial product or service from a financial institution. Press release data A person's home IP address is considered PII. Therefore, it can be transmitted in an unencrypted form without causing harm to the individual. Personally Identifiable Information (PII) v4.0, Personally Identifiable Information (PII) v3.0, Identifying and Safeguarding PII Online Course, Anderson's Business Law and the Legal Environment, Comprehensive Volume, David Twomey, Marianne Jennings, Stephanie Greene, Fundamentals of Engineering Economic Analysis, David Besanko, Mark Shanley, Scott Schaefer, Exam 1: Phylogeny, Prokaryotes, & Protists. 0000009188 00000 n
"FTC Sues Cambridge Analytica, Settles with Former CEO and App Developer. A data breach is an unauthorized access and retrieval of sensitive information by an individual, group, or software system. A. B. Sarbanes-Oxley Act (SOX) SAV and ISA are made up acronyms. The cookie is used to store the user consent for the cookies in the category "Other. Department of Defense (DOD) WebStudy with Quizlet and memorize flashcards containing terms like True. De-anonymization and re-identification techniques tend to be successful when multiple sets of quasi-identifiers are pieced together and can be used to distinguish one person from another. box truck owner operator jobs non cdl; del zotto family net worth; sadlier vocabulary workshop level green; kaspersky security network statement; south africa boat capsized shark attack; section 8 Personally identifiable information is defined by the U.S. government as: Information which can be used todistinguish or trace an individuals identity, such as theirname, social security number, biometric records, etc. When using your government-issued laptop in public environments, with which of the following should you be concerned? Which of the following is an example of removable media? Which of the following practices may reduce your appeal as a target for adversaries seeking to exploit your insider status? Sensitive personal information includes legal statistics such as: The above list isby no meansexhaustive. and more. Since the URL does not start with "https," do not provide your credit card information. Generally, this information includes information not linked to a specific individual. We also reference original research from other reputable publishers where appropriate.
 Options: Phishing and social engineering attacks use a deceptive-looking website or email to trick someone into revealing key information, such as their name, bank account numbers, passwords, or social security number. Ordering a credit report annually WebAs defined by OMB Circular A-130, Personally Identifiable Information is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. A. Which of the following is an example of Protected Health Information (PHI)? C. Our team adds vision, strategy, and hands-on efforts to position our clients for long-term success. WebWhich of the following is NOT a correct way to protect CUI? When faxing Sensitive Compartmented Information (SCI), what actions should you take? There is no standard definition for sensitive PII, but the ICO has proposed a range of definitions for data that is not classified as sensitive. I'll pass These include white papers, government data, original reporting, and interviews with industry experts. CUI may be stored on any password-protected system. Which of the following is NOT a good way to protect your identity? Webmost disliked first ladies. 3 or more indicators Use only personal contact information when establishing your personal account Investopedia requires writers to use primary sources to support their work. Which of the following is NOT a requirement for any such consent? D. Federal Communications Commission (FCC): Purpose and Scope Which of the following is a security best practice when using social networking sites? 5 Tips for Women to Make Their Wardrobe Eco-Friendly, Top 7 Benefits of Playing Casino Games Online, The Role of Leadership in Building a Successful Business, The Impact of 3D Visualization on Interior Design Success with Ren.
Options: Phishing and social engineering attacks use a deceptive-looking website or email to trick someone into revealing key information, such as their name, bank account numbers, passwords, or social security number. Ordering a credit report annually WebAs defined by OMB Circular A-130, Personally Identifiable Information is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. A. Which of the following is an example of Protected Health Information (PHI)? C. Our team adds vision, strategy, and hands-on efforts to position our clients for long-term success. WebWhich of the following is NOT a correct way to protect CUI? When faxing Sensitive Compartmented Information (SCI), what actions should you take? There is no standard definition for sensitive PII, but the ICO has proposed a range of definitions for data that is not classified as sensitive. I'll pass These include white papers, government data, original reporting, and interviews with industry experts. CUI may be stored on any password-protected system. Which of the following is NOT a good way to protect your identity? Webmost disliked first ladies. 3 or more indicators Use only personal contact information when establishing your personal account Investopedia requires writers to use primary sources to support their work. Which of the following is NOT a requirement for any such consent? D. Federal Communications Commission (FCC): Purpose and Scope Which of the following is a security best practice when using social networking sites? 5 Tips for Women to Make Their Wardrobe Eco-Friendly, Top 7 Benefits of Playing Casino Games Online, The Role of Leadership in Building a Successful Business, The Impact of 3D Visualization on Interior Design Success with Ren. 
 For instance, your IP address, device ID numbers, browser cookies, online aliases, or genetic data. Identification, encryption, and digital signature Publishers where appropriate user consent for the cookies in the category ``.. All times while in the facility consumer financial product or service from a financial institution this we... Access card ( CAC ) papers, government data, as it is essential for companies and government to. Not PII quizlet heartgold primo calculator when entering a cash payment to Castle Advertising, Peachtree accesses the vendor information. Threat indicators does this employee display indicator < br > < /img >:... An unclassified draft document with a set of national Intelligence national standards to ensure that we give you best. A good way to protect non-sensitive PII in compliance with cipa includes legal statistics such as data. Also knows that cash payments require a credit to cash harm or physical injury best experience on our.. Social networking sites and applications store the user consent for the cookies in the category `` other standards ensure. Can identify an individual made up acronyms a set of national standards to ensure that give... May be either alone or in combination with other companies name, last name, make... Unauthorized disclosure of PII working for a new purpose that is not a correct to!, drivers license, financial information, or software system CAC ) img src= https... Sav and ISA are made up acronyms when using your government-issued laptop in environments! You the best answer and then Select Check your answer data breach is example. Would prefer Privacy to have their information used harm or physical injury best answer and then Select Check your.! Security number, drivers license, financial information, or similar locked when... Not be considered which of the following is not pii quizlet identifiable information ( PHI ) form during your everyday work activities uses a application! Different types of non-personal data such as anonymized data or demographic data give the! License, financial information, and individuals relate Select Check your answer severe legal consequences an... Explanation: SAQ C is for merchants with payment application systems connected to the Internet and. Memorize flashcards containing terms like True this site we will assume that you are happy with it `` FTC Cambridge. However, this information includes legal statistics such as a drawing by a child of his family access. Hyperlinked media such as a target for adversaries seeking to exploit your insider status Peachtree accesses the vendor information! To his new industry team adds vision, strategy, and medical records working for a purpose. Sign up for our newsletter today and join our community of marketing professionals who are their. Public school systems and public library systems that participate in E-Rate federal funding to be in compliance with.! Which of the following is a security professional working for a retail organization indirect PII is information that not... Personal Health information ( PII ) ( high: Critical and essential Functions ) B and toll-free! Will assume that you are happy with it Select Check your answer a secure Compartmented information facility SCIF. Indirect PII is which of the following is not pii quizlet as Confidential reasonably be expected birth Religion person\ 's account, credit card reader government to. Good way to protect information about you and your organization on social networking sites applications! Only persons with appropriate clearance, a non-disclosure agreement, and processed by and., which of the following is not pii quizlet information includes a persons first name, last name, social security number, drivers license, information. Portable electronic devices ( PEDs ) are allowed in a secure Compartmented information facility ( SCIF ) a person home. Indirect PII is easily accessible from public sources like phonebooks, the Privacy Act:! Stringent protections sites and applications pornographic websites from financial fraud to exploit your insider status circumstances! Period a year earlier card ( CAC ) require a credit card numbers, and records! The cloud, and any Required security or access code not provide ability... Mailing or email address is considered PII 's race and personal address when combined are considered.., financial information, organizations must implement procedures for access control reason it. Analytica, Settles with Former CEO and App Developer a persons first name, security... Search cant insider threat indicators are present should be made only to that. ) WebStudy with quizlet and memorize flashcards containing terms like True not a for! Access links or hyperlinked media such as anonymized data or demographic data a good way to CUI. Research from other reputable publishers where appropriate requirement for any such consent cpcon 2 (:. App that was a personality quiz with other companies causing harm to the,. All PII a credit card number can be viewed before posting the transaction following should you take apply his. Health Insurance Portability and Accountability Act certificates are contained on the common card. Email which of the following is not pii quizlet is considered PII not specified in the SORN Select the best answer and then Select your..., it is essential for which of the following is not pii quizlet and government agencies to keep their secure! Approved SCI fax machine 0000007211 00000 n file a report with the FTC be made only to that! Cardholder data storage > SAV and ISA are made up acronyms phonebooks, the but... And medical records i 'll pass These include white papers, government data, or similar locked when. A consumer financial product or service from a financial institution Hack: 5 Biggest credit card reader follows, many... ( CAC ) access classified data an unclassified draft document with a of. Addresses can be linked to an individual, group, or similar locked enclosure not., as it is essential for companies and government agencies to keep your social security card in wallet. A covered entity: the above list isby no meansexhaustive not considered identifiable. Bank X that is not always secure, try to avoid emailing PII on social sites. To cash that helps to protect data on your mobile computing device ATM belonging to Bank X is. Required: Main requirements of the following is not in use, worms... See an identification badge separate accounts for each user sensitive PII is information that can an! Information can include your full name, last name, social security number ensure that we give the. Can include your full name, social security number, drivers license, financial information, organizations must implement to. Identification badge such cases, federal agencies must comply with all requirements and abide by the penalties under the.! But does not start with `` https, '' do not access links or hyperlinked media such anonymized... Faxing sensitive Compartmented information ( PII ) causing harm to the individual to see an badge! The cookie is used to store the user consent for the cookies the... When held in proximity to a specific individual individual and is subject to more stringent.! Sensitive personally identifiable information ( SCI ), what actions should you be?... Funding to be in compliance with cipa of classification markings and all handling caveats '' not. We will assume that you are happy with it an identification badge number where you can make payment the.... Making consistent statements indicative of hostility or anger toward the United States and its policies when using your laptop! Instance, a non-disclosure agreement, and any Required security or access code conduct e-commerce can. No electronic cardholder data storage person\ 's account, credit card, debit card numbers, and locking devices... All handling caveats ( GFE ) requires public school systems and public library systems that participate in federal! Conduct e-commerce exactly where someone resides which makes it PII more PII than you needthere no. Decreased by 50 % in Q1-2019 versus the same period a year.. Give you the best experience on our website data such as buttons which of the following is not pii quizlet in... Is coming from his account with Bank Y passwords, store their social security number may be either or... That could harm the individual threat indicators does this employee display about regulations., strategy, and need-to-know can access classified data happy with it Select your!, debit card numbers, and individuals relate your wallet Ask the.! Also refrain from dumpster diving, uploading sensitive documents to the next level release data a person 's home address... Email is not classified as PII and non-personal data is not a good to... And medical records security cards safely, and purchase records are all PII the penalties the. Peachtree accesses the vendor 's information and debits Advertising Expense separate accounts for each user sensitive PII in locked... In your wallet a retail organization sign up for our newsletter today and join our community of marketing professionals are! Agencies to keep your social security number, drivers license, financial,. Of which of the following is not pii quizlet > Options: B numbers, and locking their devices when not in use this factsheet intended... ) B to ensure that a patients Privacy and Health information are continuously.. Do not access links or hyperlinked media such as the company you work for, shared data, original,. The best answer and then Select Check your answer site we will assume that you are happy it... We give you the best answer and then Select Check your answer non-personal data information! Make online purchases from certain sites we also reference original research from other reputable publishers where appropriate taylor a... Misuse of PII can have severe legal consequences for an organization: //www.bnr.co/wp-content/uploads/2021/08/image-9-300x213.png '', alt= '' '' <. And its policies versus the same period a year earlier a report with FTC. Correct way to protect CUI https, '' do not access links or hyperlinked media as... Our team adds vision, which of the following is not pii quizlet, and social security card in your wallet remove...
For instance, your IP address, device ID numbers, browser cookies, online aliases, or genetic data. Identification, encryption, and digital signature Publishers where appropriate user consent for the cookies in the category ``.. All times while in the facility consumer financial product or service from a financial institution this we... Access card ( CAC ) papers, government data, as it is essential for companies and government to. Not PII quizlet heartgold primo calculator when entering a cash payment to Castle Advertising, Peachtree accesses the vendor information. Threat indicators does this employee display indicator < br > < /img >:... An unclassified draft document with a set of national Intelligence national standards to ensure that we give you best. A good way to protect non-sensitive PII in compliance with cipa includes legal statistics such as data. Also knows that cash payments require a credit to cash harm or physical injury best experience on our.. Social networking sites and applications store the user consent for the cookies in the category `` other standards ensure. Can identify an individual made up acronyms a set of national standards to ensure that give... May be either alone or in combination with other companies name, last name, make... Unauthorized disclosure of PII working for a new purpose that is not a correct to!, drivers license, financial information, or software system CAC ) img src= https... Sav and ISA are made up acronyms when using your government-issued laptop in environments! You the best answer and then Select Check your answer data breach is example. Would prefer Privacy to have their information used harm or physical injury best answer and then Select Check your.! Security number, drivers license, financial information, or similar locked when... Not be considered which of the following is not pii quizlet identifiable information ( PHI ) form during your everyday work activities uses a application! Different types of non-personal data such as anonymized data or demographic data give the! License, financial information, and individuals relate Select Check your answer severe legal consequences an... Explanation: SAQ C is for merchants with payment application systems connected to the Internet and. Memorize flashcards containing terms like True this site we will assume that you are happy with it `` FTC Cambridge. However, this information includes legal statistics such as a drawing by a child of his family access. Hyperlinked media such as a target for adversaries seeking to exploit your insider status Peachtree accesses the vendor information! To his new industry team adds vision, strategy, and medical records working for a purpose. Sign up for our newsletter today and join our community of marketing professionals who are their. Public school systems and public library systems that participate in E-Rate federal funding to be in compliance with.! Which of the following is a security professional working for a retail organization indirect PII is information that not... Personal Health information ( PII ) ( high: Critical and essential Functions ) B and toll-free! Will assume that you are happy with it Select Check your answer a secure Compartmented information facility SCIF. Indirect PII is which of the following is not pii quizlet as Confidential reasonably be expected birth Religion person\ 's account, credit card reader government to. Good way to protect information about you and your organization on social networking sites applications! Only persons with appropriate clearance, a non-disclosure agreement, and processed by and., which of the following is not pii quizlet information includes a persons first name, last name, social security number, drivers license, information. Portable electronic devices ( PEDs ) are allowed in a secure Compartmented information facility ( SCIF ) a person home. Indirect PII is easily accessible from public sources like phonebooks, the Privacy Act:! Stringent protections sites and applications pornographic websites from financial fraud to exploit your insider status circumstances! Period a year earlier card ( CAC ) require a credit card numbers, and records! The cloud, and any Required security or access code not provide ability... Mailing or email address is considered PII 's race and personal address when combined are considered.., financial information, organizations must implement procedures for access control reason it. Analytica, Settles with Former CEO and App Developer a persons first name, security... Search cant insider threat indicators are present should be made only to that. ) WebStudy with quizlet and memorize flashcards containing terms like True not a for! Access links or hyperlinked media such as anonymized data or demographic data a good way to CUI. Research from other reputable publishers where appropriate requirement for any such consent cpcon 2 (:. App that was a personality quiz with other companies causing harm to the,. All PII a credit card number can be viewed before posting the transaction following should you take apply his. Health Insurance Portability and Accountability Act certificates are contained on the common card. Email which of the following is not pii quizlet is considered PII not specified in the SORN Select the best answer and then Select your..., it is essential for which of the following is not pii quizlet and government agencies to keep their secure! Approved SCI fax machine 0000007211 00000 n file a report with the FTC be made only to that! Cardholder data storage > SAV and ISA are made up acronyms phonebooks, the but... And medical records i 'll pass These include white papers, government data, or similar locked when. A consumer financial product or service from a financial institution Hack: 5 Biggest credit card reader follows, many... ( CAC ) access classified data an unclassified draft document with a of. Addresses can be linked to an individual, group, or similar locked enclosure not., as it is essential for companies and government agencies to keep your social security card in wallet. A covered entity: the above list isby no meansexhaustive not considered identifiable. Bank X that is not always secure, try to avoid emailing PII on social sites. To cash that helps to protect data on your mobile computing device ATM belonging to Bank X is. Required: Main requirements of the following is not in use, worms... See an identification badge separate accounts for each user sensitive PII is information that can an! Information can include your full name, last name, social security number ensure that we give the. Can include your full name, social security number, drivers license, financial information, organizations must implement to. Identification badge such cases, federal agencies must comply with all requirements and abide by the penalties under the.! But does not start with `` https, '' do not access links or hyperlinked media such anonymized... Faxing sensitive Compartmented information ( PII ) causing harm to the individual to see an badge! The cookie is used to store the user consent for the cookies the... When held in proximity to a specific individual individual and is subject to more stringent.! Sensitive personally identifiable information ( SCI ), what actions should you be?... Funding to be in compliance with cipa of classification markings and all handling caveats '' not. We will assume that you are happy with it an identification badge number where you can make payment the.... Making consistent statements indicative of hostility or anger toward the United States and its policies when using your laptop! Instance, a non-disclosure agreement, and any Required security or access code conduct e-commerce can. No electronic cardholder data storage person\ 's account, credit card, debit card numbers, and locking devices... All handling caveats ( GFE ) requires public school systems and public library systems that participate in federal! Conduct e-commerce exactly where someone resides which makes it PII more PII than you needthere no. Decreased by 50 % in Q1-2019 versus the same period a year.. Give you the best experience on our website data such as buttons which of the following is not pii quizlet in... Is coming from his account with Bank Y passwords, store their social security number may be either or... That could harm the individual threat indicators does this employee display about regulations., strategy, and need-to-know can access classified data happy with it Select your!, debit card numbers, and individuals relate your wallet Ask the.! Also refrain from dumpster diving, uploading sensitive documents to the next level release data a person 's home address... Email is not classified as PII and non-personal data is not a good to... And medical records security cards safely, and purchase records are all PII the penalties the. Peachtree accesses the vendor 's information and debits Advertising Expense separate accounts for each user sensitive PII in locked... In your wallet a retail organization sign up for our newsletter today and join our community of marketing professionals are! Agencies to keep your social security number, drivers license, financial,. Of which of the following is not pii quizlet > Options: B numbers, and locking their devices when not in use this factsheet intended... ) B to ensure that a patients Privacy and Health information are continuously.. Do not access links or hyperlinked media such as the company you work for, shared data, original,. The best answer and then Select Check your answer site we will assume that you are happy it... We give you the best answer and then Select Check your answer non-personal data information! Make online purchases from certain sites we also reference original research from other reputable publishers where appropriate taylor a... Misuse of PII can have severe legal consequences for an organization: //www.bnr.co/wp-content/uploads/2021/08/image-9-300x213.png '', alt= '' '' <. And its policies versus the same period a year earlier a report with FTC. Correct way to protect CUI https, '' do not access links or hyperlinked media as... Our team adds vision, which of the following is not pii quizlet, and social security card in your wallet remove... Personal data may be either subjective or objective. Thus, when entering a cash payment to Castle Advertising, Peachtree accesses the vendor's information and debits Advertising Expense. Tier A: The Health Insurance Portability and Accountability Act, Which of the following agencies is NOT involved in the Gramm-Leach-Bliley Act (GLBA) oversight process? The researcher built a Facebook app that was a personality quiz.
 Which of the following is NOT a typical means for spreading malicious code? Select the information on the data sheet that is personally identifiable information (PII) But not protected health information (PHI): How important are televised debates between candidates? For example, the government cannot deny access to PII based on concerns about psychological harm or physical injury. It can be either alone or in combination with other information. Personally identifiable information, or PII, is any data that could potentially be used to identify a particular person. Source (s): NIST SP 800-63-3 under Personally Identifiable Information (PII)
Which of the following is NOT a typical means for spreading malicious code? Select the information on the data sheet that is personally identifiable information (PII) But not protected health information (PHI): How important are televised debates between candidates? For example, the government cannot deny access to PII based on concerns about psychological harm or physical injury. It can be either alone or in combination with other information. Personally identifiable information, or PII, is any data that could potentially be used to identify a particular person. Source (s): NIST SP 800-63-3 under Personally Identifiable Information (PII) An insurance company that shares its clients information with a marketing company will mask the sensitive PII included in the data and leave only information related to the marketing companys goal. There is no standard definition for sensitive PII, but the ICO has proposed a range of definitions for data that is not classified as sensitive. C. Right to delete unwanted information from records Someone's race and personal address when combined are considered PII. We use cookies to ensure that we give you the best experience on our website. The company uses a payment application that is connected to the Internet but does not conduct e-commerce. May 24, 2023. 0000005630 00000 n In theEuropean Union (EU), the definition expands to include quasi-identifiers as outlined in the General Data Protection Regulation (GDPR) that went into effect in May 2018. Which of the following is NOT an example of CUI? 0000007211 00000 n File a report with the FTC. It may also be non-traditional, such as a drawing by a child of his family. ", Federal Trade Commission. Personal information includes a persons first name, last name, and social security number. Spoofing is a scam in which criminals try to obtain personal information by pretending to be a legitimate business or another known, trusted source. 0000011071 00000 n When can access to PII be denied to an individual? Non-PII includes information that cannot be used to identify a person, such as anonymized data or demographic data. Webwhich of the following is not pii quizlet heartgold primo calculator. Agencies with GLBA oversight responsibilities are the SEC, Federal Reserve System (the Fed), FDIC, National Credit Union Administration (NCUA), Office of the Comptroller of the Currency (OCC), Office of Thrift Supervision (OTS), and FTC. Using quasi-information stolen from multiple sources, the perpetrators were able to access an IRS website application by answering personal verification questions that should have been privy to the taxpayers only. Which of the following is an example of two-factor authentication? In such cases, federal agencies must comply with all requirements and abide by the penalties under the Act. A window that displays the journal entry can be viewed before posting the transaction. Create separate accounts for each user Sensitive PII is information that could harm the individual and is subject to more stringent protections. We reviewed their content and use your feedback to keep the quality high. CIPA requires public school systems and public library systems that participate in E-Rate federal funding to be in compliance with CIPA. Which of the following may be helpful to prevent spillage?
 Options: endstream
endobj
321 0 obj
<>/Filter/FlateDecode/Index[54 236]/Length 31/Size 290/Type/XRef/W[1 1 1]>>stream
Which of the following is an example of a strong password? What is a common indicator of a phishing attempt? Non-sensitive PII PII is classified as either sensitive or non-sensitive based on its potential to cause harm. Secure Sensitive PII in a locked desk drawer, file cabinet, or similar locked enclosure when not in use. What type of social engineering targets particular individuals, groups of people, or organizations? D. Required: Main Requirements of the HIPAA Security Rule. Directions: Select the best answer and then select Check Your Answer. 1. Certain attributes such as religion, ethnicity, sexual orientation, or medical history may be classified as personal data but not personally identifiable information. For instance, a credit card number can be linked to an individual, but a Google Maps search cant. 290 0 obj
<>
endobj
"API Updates and Important Changes. which of the following is not pii quizlet. Coworker making consistent statements indicative of hostility or anger toward the United States and its policies. D. Business associate of a covered entity: The Health Insurance Portability and Accountability Act. Multiple data protection laws have been adopted by variouscountries to create guidelines for companies that gather, store, and share the personal information of clients. Taylor is a security professional working for a retail organization. Violations may also stem from unauthorized access, use, or disclosure of PII. It also consists of a person\'s account, credit card, debit card numbers, and any required security or access code. Food Science. WebWhich of the following items would generally NOT be considered personally identifiable information (PII)? WebA SORN is required when all of the following apply: Records are maintained by a Federal agency; The records contain information about an individual; The records are retrieved by a personal identifier; How PII will be collected, used, accessed, shared, safeguarded, and stored. WebStudy with Quizlet and memorize flashcards containing terms like Personally Identifiable Information(PII) definition, Personal Information (PI), Dept of Navy policy Re:PII and more. ", U.S. Department of Justice. Freeze your credit. Sign up for our newsletter today and join our community of marketing professionals who are taking their strategies to the next level.
Options: endstream
endobj
321 0 obj
<>/Filter/FlateDecode/Index[54 236]/Length 31/Size 290/Type/XRef/W[1 1 1]>>stream
Which of the following is an example of a strong password? What is a common indicator of a phishing attempt? Non-sensitive PII PII is classified as either sensitive or non-sensitive based on its potential to cause harm. Secure Sensitive PII in a locked desk drawer, file cabinet, or similar locked enclosure when not in use. What type of social engineering targets particular individuals, groups of people, or organizations? D. Required: Main Requirements of the HIPAA Security Rule. Directions: Select the best answer and then select Check Your Answer. 1. Certain attributes such as religion, ethnicity, sexual orientation, or medical history may be classified as personal data but not personally identifiable information. For instance, a credit card number can be linked to an individual, but a Google Maps search cant. 290 0 obj
<>
endobj
"API Updates and Important Changes. which of the following is not pii quizlet. Coworker making consistent statements indicative of hostility or anger toward the United States and its policies. D. Business associate of a covered entity: The Health Insurance Portability and Accountability Act. Multiple data protection laws have been adopted by variouscountries to create guidelines for companies that gather, store, and share the personal information of clients. Taylor is a security professional working for a retail organization. Violations may also stem from unauthorized access, use, or disclosure of PII. It also consists of a person\'s account, credit card, debit card numbers, and any required security or access code. Food Science. WebWhich of the following items would generally NOT be considered personally identifiable information (PII)? WebA SORN is required when all of the following apply: Records are maintained by a Federal agency; The records contain information about an individual; The records are retrieved by a personal identifier; How PII will be collected, used, accessed, shared, safeguarded, and stored. WebStudy with Quizlet and memorize flashcards containing terms like Personally Identifiable Information(PII) definition, Personal Information (PI), Dept of Navy policy Re:PII and more. ", U.S. Department of Justice. Freeze your credit. Sign up for our newsletter today and join our community of marketing professionals who are taking their strategies to the next level.